The term “biometrics” is derived from the Greek words bio (life) and metric (to measure). Biometrics refers to technologies for measuring and analyzing a person’s physiological or behavioral characteristics such as fingerprints, irises, voice patterns, facial patterns, and hand measurements, for identification and verification purposes. [5] Since these characteristics are unique to each
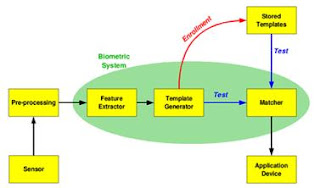
Figure 1: General biometrics block diagram. [4]
There are two types of biometrics characteristic that are behavioral and physiological. Behavioral biometric are generally used for verification while physiological biometrics can be used for either identification or verification. Furthermore, behavioral biometric is defined by analyzing a specific action of a person whereas physiological biometric use an algorithm to define identity from a direct measurement of human physical asset. The examples of physiological biometrics are fingerprint, facial recognition, hand geometry, iris scan, retinal scan vascular patterns and DNA. The speaker or voice recognition, signature and keystroke are instead the example of behavioral biometrics. [3, 5, 11] The entire biometrics are basically measuring and analyzing the unique physical and behavior of a human.
2.1.Fingerprint
Fingerprint technology is the technology that analyzing fingertip patterns. It can be used for both verification as well as identification. Electronic fingerprint matching can be achieved through one of two methodologies. The first uses the ridge endings and bifurcation’s on a person’s finger to plot points known as Minutiae (Minutiae based approach). These Minutiae allow for a comparison of two fingerprints to be achieved electronically. The second methodology uses a pattern based approached. This comparison technique (Pattern based) is performed in two fundamental blocks that are image Enhancement and Distortion Removal. In each instance that a finger is applied to a fingerprint device, the ridge pattern exhibits a different degree of distortion. [11]
2.2.Facial
Face recognition technology is a technology that measuring facial characteristic. It is also known as a biometrics technology that uses an image or series of images either from camera or photograph to recognize a person. Unlike other biometrics technologies, face recognition is a passive biometrics and does not require a person’s cooperation. It can recognize people from a distance without them realizing that they are being analyzed. Some technologies use an algorithm called LFA (Local Feature Analysis) to identify and derive a representation in terms of the spatial relationships between irreducible local features, or ‘nodal points’ on the face. Others use an approach known as Eigenfaces while some use as advanced neural network technology to recognize faces electronically. [11]
2.3.Hand Geometry
Hand geometry technology is a technology that measuring the shape of the hand. The user places the palm of their hand on a metal surface which has guidance pegs on it. The hand is properly aligned by the pegs so the device can read the hand attributes. [5] It is systems that are commonly available in two main forms. Full hand geometry systems take an image of the entire hand for comparison while Two Finger readers only image two finger of the hand. [11] Unlike fingerprints, the human hand is not unique thus individual hand features are not descriptive enough for identification but it can be used for verification system. [5]
2.4.Iris Scan
Iris recognition is a biometrics technology that analyzing features of colored ring, furrows and freckles of the eye. It uses a camera, much like face recognition does to capture an image of the iris and then convert that image to a template using complex algorithms and 2D Gabor Wavelets. The user places them so that they can see their own eye’s reflection in the device. The user may be able to do this from up to 2 feet away depending on the device because iris recognition has become more passive and it’s also capable of performing 1: many matches at extraordinary high speeds without sacrificing accuracy. [5, 11]
2.5.Speaker/Voice
Speaker recognition is a technology that analyzing vocal or voice behavior. The user speaks into microphone their password or access phrase. [5] The microphone is then vibrated as per user speaks and produce an electrical wave. This electrical wave is then been analyzed and outputting the verification result. The system can only be used for identity verification system because the voices are not really unique to identify a person.
Biometrics can furthermore be defined as either active or passive biometrics. Active and passive generally means how the system will work either with people helps or its can perform analysis and recognition by its own. In contrast, active biometric do require a person cooperation and will not work if they deny their participation in the process and passive biometrics technology however, do not require a users active participation and can be successful without a person even knowing they have been analyzed. In order to illustrate further, the voice recognition (limited), iris recognition (limited) and facial recognition technologies are among passive biometric while fingerprint, hand geometry, retina scanning and signature technologies are fall under active biometric categories. [11]
Biometric technologies are one of the recognition systems to recognize people based on identifying or verifying the unique biological asset that belong to them. Recognition does not necessarily imply either verification or identification, but noted that all biometric systems perform “recognition” to “again know” a person who has been previously enrolled. [5]
Identification is a task where it involves establishing a person’s identity based only on biometric measurements. The comparator matches the obtained biometric with the one stored in the database bank using a 1: N matching algorithm for identification. [1] In contrast, it can be understand by taking an example of police road block analogy. At the road block, the policeman stops the car and by taking a simple example that in this situation he can recognize the driver because the driver is his close friend. Thus without asking the driver’s name, he already knows who the driver name is and maybe just asking for the license only. From this situation, the biometric measurement here is probably face recognition and the database bank is obviously the policeman’s brain. For 1: N matching algorithm in this situation is the process of the policeman recognize this driver while in his brain there are more friend’s faces to be differentiated.
Verification on the other hand involves confirming or denying a person’s claimed identity. A basic identity (e.g. ID number) is accepted and a biometric template of the subject taken is matched using 1: 1 matching algorithm to confirm the person’s identity. [1] By taking the same example of a police road block analogy above, but this time the policeman cannot recognize the driver because he never meet him. Therefore the policeman will ask the driver to give some ID (normally Identification Card (IC)) together with his license so that he can verify the driver claimed identity. From this situation, the basic identity is the picture in the driver’s IC and the biometric template of the subject is the driver’s face viewed by the policeman’s eyes. For 1: 1 matching algorithm in this situation is the process of the policeman comparing between the picture in the IC and the real driver’s face that he saw. If the faces are almost the same, the driver is verified to be the person who the driver claimed to be.

Figure 2: Biometrics comparison chart. [9]
From the biometric comparison char above, it is clearly can be seen that verification is applicable for all biometric, but not for identification. One of the factors that identification cannot be applied to a certain biometric technologies is due to its accuracy of recognizing people using 1: N matching algorithm. Human beings are also having difficulties to identify people based on facial, hand geometry and voice. Some of the analogies here are sometimes people do mistake identifying a twin sibling and people was being cheated by anonymous phone caller pretending as a bank officer. Eventually, the uniqueness of everyone’s biometric can sometimes be different from what has been recorded during enrollment due to their age, environment and healthiness.
5. REFERENCES
1. Suddhesh Angle, Reema Bhagtani, Hemali Chheda. Biometrics: A Further Echelon of Security. http://eref.uqu.edu.sa/files/eref2/folder1/biometrics__a_further_echelon_of_securit_89264.pdf. 2.51PM Aug 5, 2009.
2. Biometrics Catalog. http://www.biometricscatalog.org/Introduction/Default.aspx? sindex=0. 4.03PM Aug 5, 2009.
3. Types of Biometrics. www.cse.unr.edu/~bebis/CS790Q/Lect/Chapters_3_4.ppt.
4.30PM Aug 5, 2009.
4. Biometrics. http://en.wikipedia.org/wiki/Biometrics. 2.32PM Aug 5, 2009.
5. An Overview of Biometrics. http://ctl.ncsc.dni.us/biomet%20web/BMIndividuals.html. 3.11 PM Aug 5, 2009.
6. Biometric Identification Systems. http://www.alwanat.com/Biometric_Identification.html
3.29PM Aug 6, 2009.
7. Fingerprint Technology. http://itblogs.in/biometrics/bio-metrics/ 3.26PM Aug 6, 2009.
8. Biometrics Encryption. http://www.emory.edu/BUSINESS/et/biometric/Index.htm 2.45PM Aug 5, 2009.
9. Biometrics Comparison Chart. http://ctl.ncsc.dni.us/biomet%20web/BMCompare.html
3.03PM Aug 5, 2009.
10. A Touch of Money. http://www.engr.sjsu.edu/wbarrett/JainSpectrum.htm
3.37PM Aug 6, 2009.
11. About Biometrics. http://www.biocom.tv/Index.htm 3.18PM Aug 5, 2009.
12. Cafeteria Management System. http://www.cenmetrix.lk/cafeteria_management _system.htm. 1.48PM Aug 6, 2009.
13. Access Control. http://www.necel.com/applications/en/industry/building/fire/ac /index.html. 10.14PM Aug 6, 2009.
14. Automated Time and Attendance System. http://automated-machines.com/automated-time-and-attendance-system.html. 2.25PM Aug 13, 2009.
15. Immigration Multimodal Biometrics. https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEisEphNc-bgbnGg7rCXVZNWcLDIUeLc3W7WETB4_EUgq35j-bfLFeeqf402Piaz62n5-9vaUYFdJbZZa-Ij7SNruTrR0fFi0U29D43p5o4vHyFhwg8K284Jk6hyYtJWSXG7uRUgeWpsE5p3/s1600-h/adv_03.gif.
3.03PM Aug 13, 2009.
16. System for Biometric Authorization of Internet Users Based on Fusion of Face and Palmprint Features. http://www.zemris.fer.hr/projects/Biometrics/english/results.shtml
2.24PM Aug 13, 2009.
17. The Fingerprint Project. http://www.ibrtses.com/projects/fingerprint.html.
2.29PM Aug 6, 2009.
18. System Block Diagram: Fingerprint Biometrics. http://focus.ti.com/vf/docs/blockdiagram.tsp?family=vf&blockDiagramId=6020.
10.44 AM Aug 6, 2009.
19. Network Biometrics Authentication. http://instruct1.cit.cornell.edu/courses/ee476 /FinalProjects/s2008/pag42_msr53/pag42_msr53/index.htm#design. 3.59PM Aug 6, 2009.
20. Passive Fingerprint. http://tutorial.msamir.net/passive-fingerprint.html.
3.12 PM Aug 6, 2009.
21. Fingerprint Recognition. http://www.barcode.ro/tutorials/biometrics/fingerprint.html
3.40PM Aug 6, 2009
22. Capacitive Fingerprint Sensor. http://www-micro.deis.unibo.it/~tartagni/Finger/FingerSensor.html 3.46PM Aug 6, 2009.
23. Camera-Based ID Verification by Signature Tracking. http://www.vision.caltech.edu/mariomu/research/sigverif/. 2.19PM Aug 13, 2009.
24. Fingerprint Scanners. http://www.tech-faq.com/fingerprint-scanners.shtml
12.21PM Aug 6, 2009.
25. How Stuff Work. http://computer.howstuffworks.com/fingerprint-scanner3.htm 11.40PM Aug 6, 2009.
26. How Stuff Work. http://computer.howstuffworks.com/fingerprint-scanner2.htm 11.44AM Aug 6, 2009.

















1 comments:
That was an excellent article about biometrics. Biometric Security Technology is now becoming part of
our everyday life as Governments and Business seeks to adapt Biometric Technology to make us safer from treats of terrorism and identity fraud, thus Biometric technology
is filtering down to you the consumers in the form of Biometric door lock, Fingerprint Readers in the form of fingerprint door locks, Biometric Time Attendance,Biometric car security systems,etc
Post a Comment